Tags: volatility
Rating:
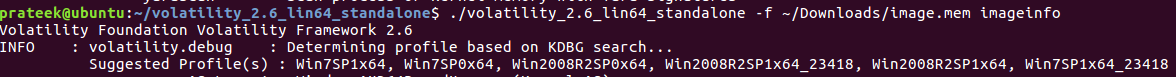
First, we check the operating system info by using the imageinfo plugin of Volatility.
Listing the running processes on the image we can see the notepad application's process. And the challenge name leads me to believe that the notepad application is the one we need to check out. Now all we have to do is find the name of the file open on Notepad and read its contents.
Volatility2 has a couple of plugins for finding the open files and dumping their contents: filescan and dumpfiles. Dumping the contents of the passwords.txt file, we can see that it is base64 encoded and decoding it gives the flag.
[Original writeup](https://fubswr55.gitbook.io/ctf/umassctf-21) (https://fubswr55.gitbook.io/ctf/umassctf-21)