Tags: web
Rating: 5.0
**Category: Web Points: 700**
> crackme! http://95.85.55.168/vmctf.html
## Writeup
**The first step is to deobfuscate the variable names**
Script: fix_coco.py
Output: `vmctf2.html`
As you can see in `vmctf2.html` the functionality that processes the password is vmed
`GetFlag.var_20_` represents the bytecode
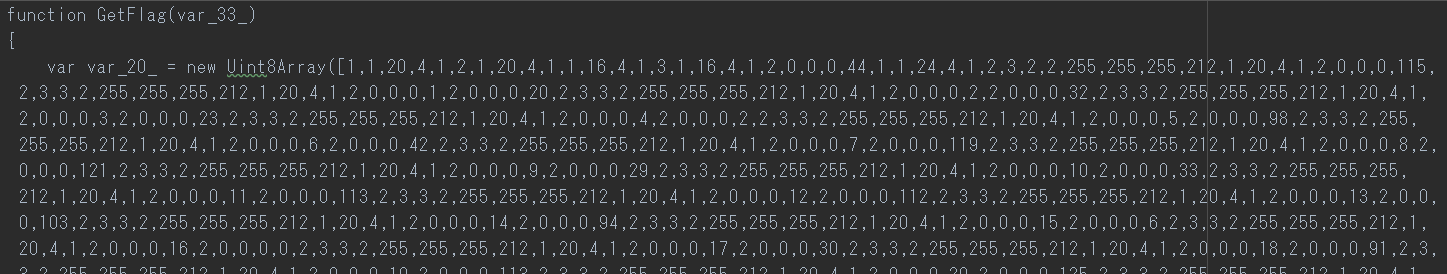
`var_19_.var_5_()` represents the method to fetch 1 instruction byte
`var_19_.var_28_()` dispatches the byte code to the corresponding handler
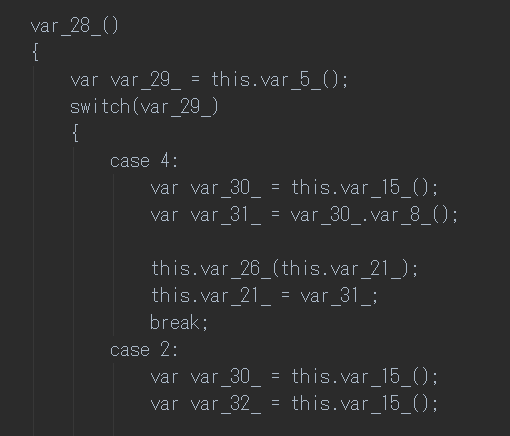
Each handler represents an x86 instruction
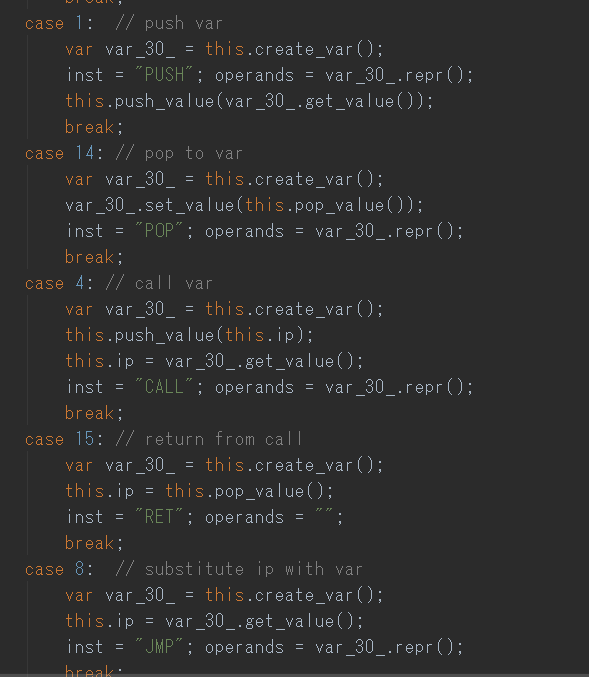
**Log the behavior in every handler to obtain a better understanding**
Script: `trace.js`
Output: `runtrace.txt`
Variables and classes are renamed in trace.js for the sake of visual aid
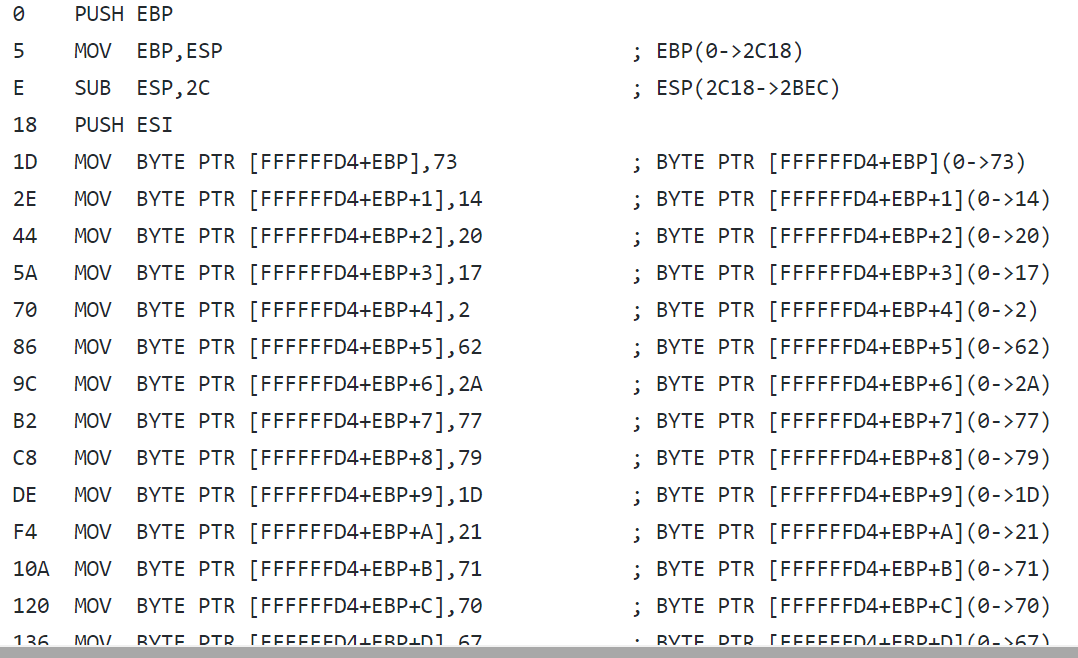
**Create another script that disassembles the vmed code from top to bottom by not executing JMPs**
Script: `disasm.js`
Output: `disasm.txt`
Note that in order to get an accurate disassembly, the constructor of class `Memory` has to be modified to
save the registers and offsets of the operand for later reference.
**Rewrite the disassembly to C++**
Output: `decompile.cpp`
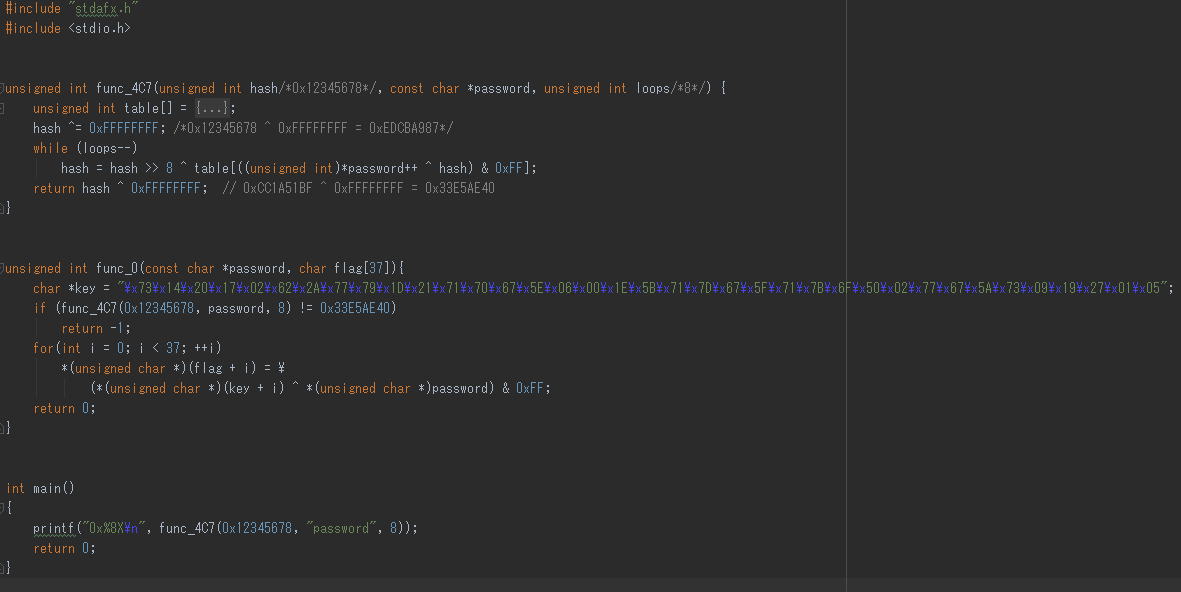
As seen in `decompile.cpp`, `func_4C7` creates a hash-like value of the password and if it matches with 0x33E5AE40,
the flag is generated and returned to the user
Creating an inverse function of `func_4C7` is not feasible.
However, we do know that the flag starts with `"KLCTF"` according to the ctf homepage and
we also know that it's derived from the password with a simple xor with a fixed key(`func_0.key`).
Therefore the first 5 characters of the password can be computed by XORing `func_0.key` and `"KLCTF"`.
The 3rd parameter in `func_4C7` representing the number of iterations is 8 implying the password length.
This leaves us with 3 characters and 100^3 different combinations which can be easily bruteforced.
Can you will make a youtube video or a details explanation for this problem....its a little bit confusing...i am not understanding...
Motivation is the component which we will do anything so it is verify that with assist of our will we do many splendid things. Many specialists do work to provide an explanation for <a href="https://uk.gowork.com">reviews about employers</a> motivation in element to the people. We want such motivations to do paintings in our existence and to make something for us and for others..
While we are making a website and in this website you can think more for our working. This working is showing us positive reaction then it was good for the people and also for their publicity of their <a href="https://www.assignmentgeek.com.au/dissertation/">assignmentgeek dissertation</a> work so that was a true way which is providing us some new pages.
Hi to everybody, here everyone is sharing such knowledge, so it’s fastidious to see this site, and I used to visit this blog daily <a href="https://www.naturalfoodseries.com/11-herbs-lose-weight">Weight Loss Herbs</a>
Thanks for sharing this information. I really like your blog post very much. You have really shared a informative and interesting blog post with people.. <a href="https://www.naturalfoodseries.com/11-healthy-foods-high-zinc">Zinc Food Source</a>
I’ve read some good stuff here. Definitely worth bookmarking for revisiting. I surprise how much effort you put to create such a great informative website. <a href="https://www.naturalfoodseries.com/15-foods-rich-protein">Protein Food Source</a>
They're produced by the very best degree developers who will be distinguished for your polo dress creating. You'll find polo Ron Lauren inside exclusive array which include particular classes for men, women. <a href="https://www.naturalfoodseries.com/egg-york-nutrition-health-risk">Egg York</a>
I want you to thank for your time of this wonderful read!!! I definately enjoy every little bit of it and I have you bookmarked to check out new stuff of your blog a must read blog! <a href="https://www.naturalfoodseries.com">Health Benefits</a>
I would like to thank you for the efforts you have made in writing this article. I am hoping the same best work from you in the future as well.. <a href="https://www.naturalfoodseries.com/13-benefits-hummus">Hummus</a>
I’ve read some good stuff here. Definitely worth bookmarking for revisiting. I surprise how much effort you put to create such a great informative website. <a href="https://www.naturalfoodseries.com/13-benefits-drinking-kombucha-every-day">Kombucha</a>
We are really grateful for your blog post. You will find a lot of approaches after visiting your post. Great work <a href="https://www.naturalfoodseries.com/13-health-benefits-coffee">Coffee</a>
Its a great pleasure reading your post.Its full of information I am looking for and I love to post a comment that "The content of your post is awesome" Great work. <a href="http://digitalexpressmastering.com/cd-dvd-printing/">custom printed cds</a>
When your website or blog goes live for the first time, it is exciting. That is until you realize no one but you and your. <a href="http://www.compositedoors2you.co.uk/">Composite Doors 2 You Shropshire</a>
My Essay Writer is the go-to source for the completion of academic assignments. If you are screaming out “<a href="https://www.myessaywriter.net/">write my essay for me</a>,” you’ve come to the most elite essay writing service
I can see that you are an expert at your field! I am launching a website soon, and your information will be very useful for me.. Thanks for all your help and wishing you all the success in your business. <a href="https://essaygenerators.com">essaygenerators.com</a>
Your work is very good and I appreciate you and hopping for some more informative posts <a href="https://www.linfield.edu/chaplain/area-churches.html">Church on the hill mcminnville oregon</a>
I love the way you write and share your niche! Very interesting and different! Keep it coming! <a href="https://www.fullycoveredagent.com/">Insurance Marketing</a>
Truly, this article is really one of the very best in the history of articles. I am a antique ’Article’ collector and I sometimes read some new articles if I find them interesting. And I found this one pretty fascinating and it should go into my collection. Very good work! <a href="https://www.youtube.com/watch?v=xFiPdkHwyRU&feature=youtu.be">Veterans slam Trump for border 'stunt</a>
Truly, this article is really one of the very best in the history of articles. I am a antique ’Article’ collector and I sometimes read some new articles if I find them interesting. And I found this one pretty fascinating and it should go into my collection. Very good work! <a href="https://www.youtube.com/watch?v=xFiPdkHwyRU&feature=youtu.be">Veterans slam Trump for border 'stunt</a>
I love the way you write and share your niche! Very interesting and different! Keep it coming! <a href="https://www.fullycoveredagent.com/">Insurance Marketing</a>
He just lives as if he never died. Just enjoy it, rest ... it begs to be bet like game: <a href="http://happy-wheelsgames.com">happy wheels</a> <a href="http://happy-wheelsgames.com/basketball-legends-game">basketball legends game</a>
The web site is lovingly serviced and saved as much as date. So it should be, thanks for sharing this with us. <a href="https://vipconsumerfinancing.com/">Consumer Financing</a>
I have read your article, it is very informative and helpful for me.I admire the valuable information you offer in your articles. Thanks for posting it.. <a href="https://educafitcurso.com.br/">educafit</a>
Very interesting blog. Alot of blogs I see these days don't really provide anything that I'm interested in, but I'm most definately interested in this one. Just thought that I would post and let you know. <a href="https://www.marketing1on1.com/local-seo-services/">rank your Local Business</a>
Through this post, I know that your good knowledge in playing with all the pieces was very helpful. I notify that this is the first place where I find issues I've been searching for. You have a clever yet attractive way of writing. <a href="https://mashable.com/shopping/oct-18-cbd-gummies-sale/#x3dpAULsRZq3">cbd gummies</a>
Through this post, I know that your good knowledge in playing with all the pieces was very helpful. I notify that this is the first place where I find issues I've been searching for. You have a clever yet attractive way of writing. <a href="https://showboxmovies.co/">Showbox</a>
I think about it is most required for making more on this get engaged <a href="https://kryztoff895807521.wordpress.com/2018/11/10/videtar-pro-video-software-and-oto-review-read-this-before-you-buy/">marketing online</a>
I read that Post and got it fine and informative. Please share more like that... <a href="https://gigolette88.tumblr.com/">Land Clearing Companies in Virginia</a>
It's late finding this act. At least, it's a thing to be familiar with that there are such events exist. I agree with your Blog and I will be back to inspect it more in the future so please keep up your act. <a href="https://spo-prime.info/">먹튀사이트</a>
Thank you for helping people get the information they need. Great stuff as usual. Keep up the great work!!! <a href="http://www.scoutstervuren.com/">Education Consulting Technology</a>
Great tips and very easy to understand. This will definitely be very useful for me when I get a chance to start my blog. <a href="https://www.sellcoins.ae/">buy BitCoin in uae</a>
Great tips and very easy to understand. This will definitely be very useful for me when I get a chance to start my blog. <a href="https://www.youtube.com/watch?v=bOnoYnno_QQ">secrid wallet deutsch</a>
This is very educational content and written well for a change. It's nice to see that some people still understand how to write a quality post! <a href="https://www.kronrex.com/">3D printer filament carbon fiber</a>
This is very educational content and written well for a change. It's nice to see that some people still understand how to write a quality post! <a href="https://www.kronrex.com/">3D printer filament carbon fiber</a>
I think I have never seen such blogs ever before that has complete things with all details which I want. So kindly update this ever for us. <a href="http://www.uspasecurity.com/">Security guard company</a>
I have read your article, it is very informative and helpful for me.I admire the valuable information you offer in your articles. Thanks for posting it.. <a href="https://bodiesinmotion.com/">Bodies in Motion</a>
Great tips and very easy to understand. This will definitely be very useful for me when I get a chance to start my blog. <a href="http://hotelhagakristineberg.se/">Mer om Wordpress</a>
A debt of gratitude is in order for the blog entry amigo! Keep them coming... <a href="https://www.yelp.com/biz/church-on-the-hill-mcminnville">Church on the hill</a>
I read your post and I found it amazing! thank! <a href="http://www.ispace1.com/">long distance relationship</a>
For bathroom renovation contractors that specialize in bathroom remodelling and design get the pros at bathroom remodel Vancouver. For great prices and professional workmanship from the plumbing to the tile and everything in between. Serving Vancouver for many years and delivering the best bathrooms in Vancouver area. <a href="http://bathroomremodel.ca/">Bathroom Reno Vancouver</a>
Best Realtors in Surrey to list your home or condo. A Chinese speaking Realtor that can converse in Mandarin, Cantonese, and English. A Top 1% PREC Team Member for over 10 years in a row. A Team that knows how to get the best deal for you through negotiations and knowledge of Surrey Real Estate. <a href="https://www.surreyhome4sale.com/">Surrey Real estate</a>
I found Hubwit as a transparent s ite, a social hub which is a conglomerate of Buyers and Sellers who are ready to offer online digital consultancy at decent cost. <a href="http://www.zlimonc.com/concord-nc-limousine-service/">Concord Limousine Service</a>
I’m excited to uncover this page. I need to to thank you for ones time for this particularly fantastic read !! I definitely really liked every part of it and i also have you saved to fav to look at new information in your site. <a href="https://www.bathbombbootcamp.com/">https://www.bathbombbootcamp.com</a>
I want to say thanks to you. I have bookmark your site for future updates. <a href="https://wearproofbrands.com/">military grade wool socks</a>
I am impressed by the information that you have on this blog. It shows how well you understand this subject. <a href="https://www.serviceprofessionalsnetwork.com/social-media-police-build-brand/">social media</a>
Good work! I am glad to thank you for this informative program which helps me and solve my problem. I suggest making more website on a cheap rate by of coding so anyone like me takes avail of this type of blog. If anyone has interests in SEO. We provide them the training at SEO institute in rohini. They will come to get trained.