Tags: forensics networking
Rating: 4.0
# **That’s Not My Name”(Forensic) — DownUnderCTF 2021**
The main goal of "That's Not My Name" was find the exfiltration DNS packet that contained the flag
# **Analisys**
For a complete analisys of the DNS Exfiltration visit this link and the solution [https://medium.com/@leonuz/](https://medium.com/@leonuz/thats-not-my-name-forensic-challenge-writeup-downunderctf-2021-cc8211b6f60b)
# **Unintended solution**
In Wireshark, we look up DNS and notice that the strange strings are Hexadecimal, then we do the following:
1)DUCTF{ → to HEX = 44554354467b
2) in Wireshark we look for that HEX string and copy its value
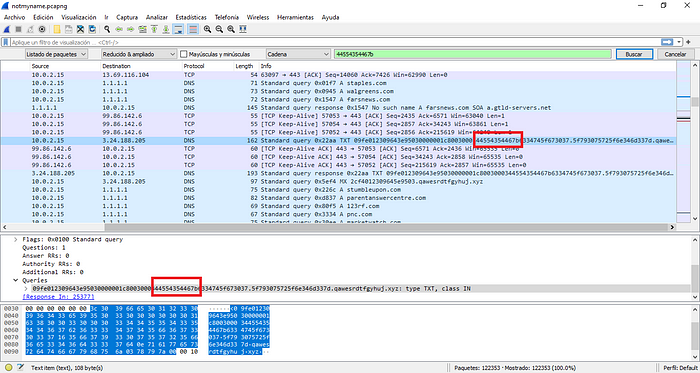
3) then paste the value in CyberChef and decode from HEX
4) we got the flag
DUCTF{c4t_g07_y0ur_n4m3}